For this I can thank the existence of electronic wallets or e-wallets for short. As many people know, an e-wallet is a digital tool for transferring funds or making transactions for goods and services. Within an e-wallet, I can store credit… Read More
Whitepapers
V-Key Technology Whitepaper
Get an in-depth look at the technology behind V-Key’s world-class, digital security solutions. V-Key’s CTO Er Chiang Kai and his team have released an updated whitepaper detailing a comprehensive overview of V-Key V-OS and the various product families that complement it:… Read More
Most Mobile Authentication Apps Can be Breached, Even if Hardware Security is Used
New research from V-Key reveals a critical flaw (“Trust Gap”) in most mobile authentication apps, putting your accounts at risk. Even hardware security features might not be enough to protect you from malicious attacks. Download the white paper to: Understand the limitations of… Read More

V-Key RASP whitepaper
Fortify Your Mobile Apps: V-Key RASP Whitepaper on Next-Gen Security Mobile apps face unique security challenges. Traditional methods might not be sufficient in untrusted environments where compromised devices are a potential hazard. V-Key’s RASP offers a powerful defense against these threats. Download the V-Key… Read More

How to survive a hacking attack?
A data breach can be devastating – lost customer trust, financial penalties, and reputational damage. This white paper equips you with 10 essential questions to evaluate your mobile security system and ensure your app survives a hacking attempt. Uncover your vulnerabilities… Read More
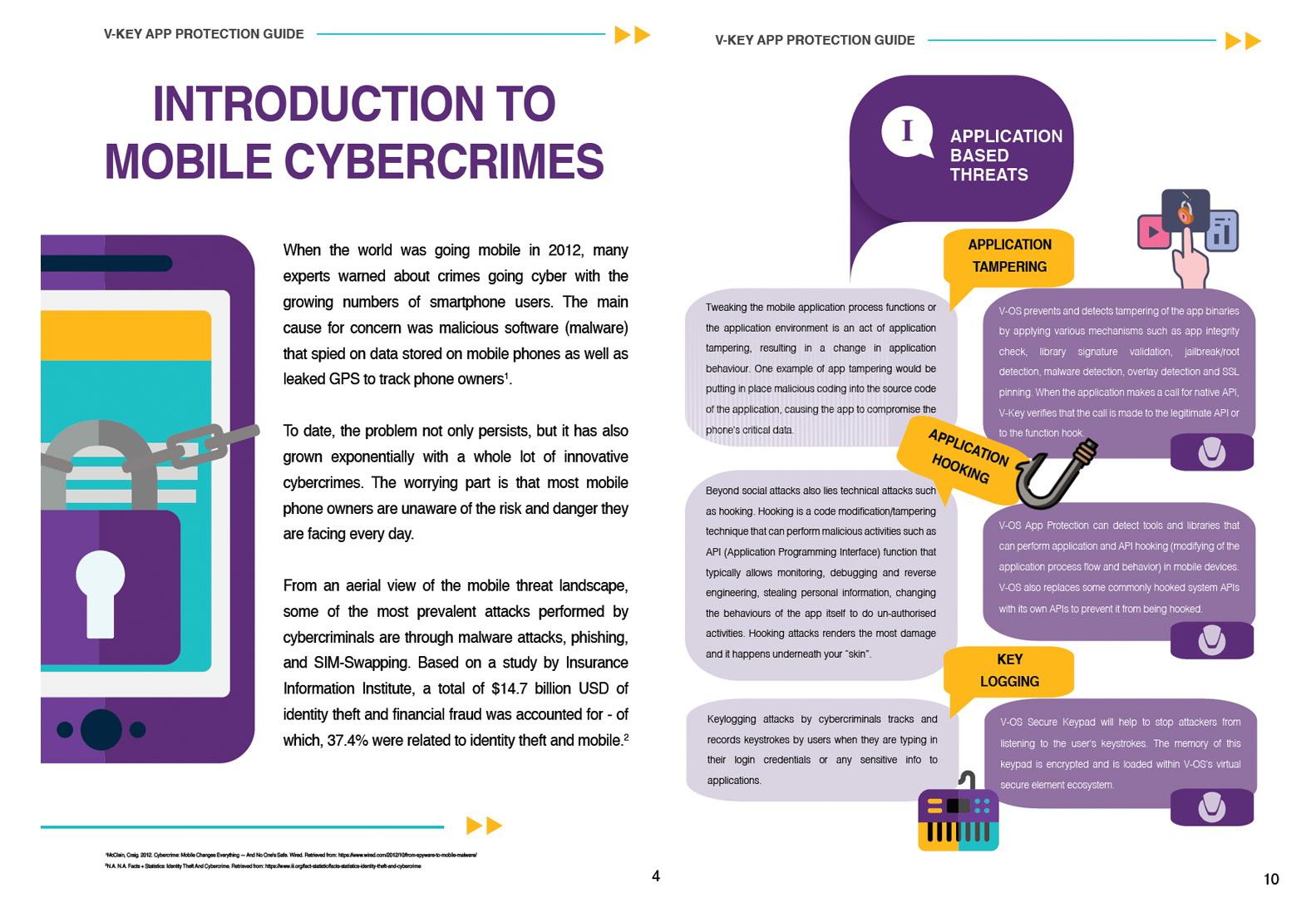
App Protection Guide
Today’s smartphones hold a wealth of sensitive data – banking information, personal documents, and more. Cybercriminals are constantly developing new methods to exploit these vulnerabilities, putting your privacy and security at risk. This white paper will equip you with the… Read More
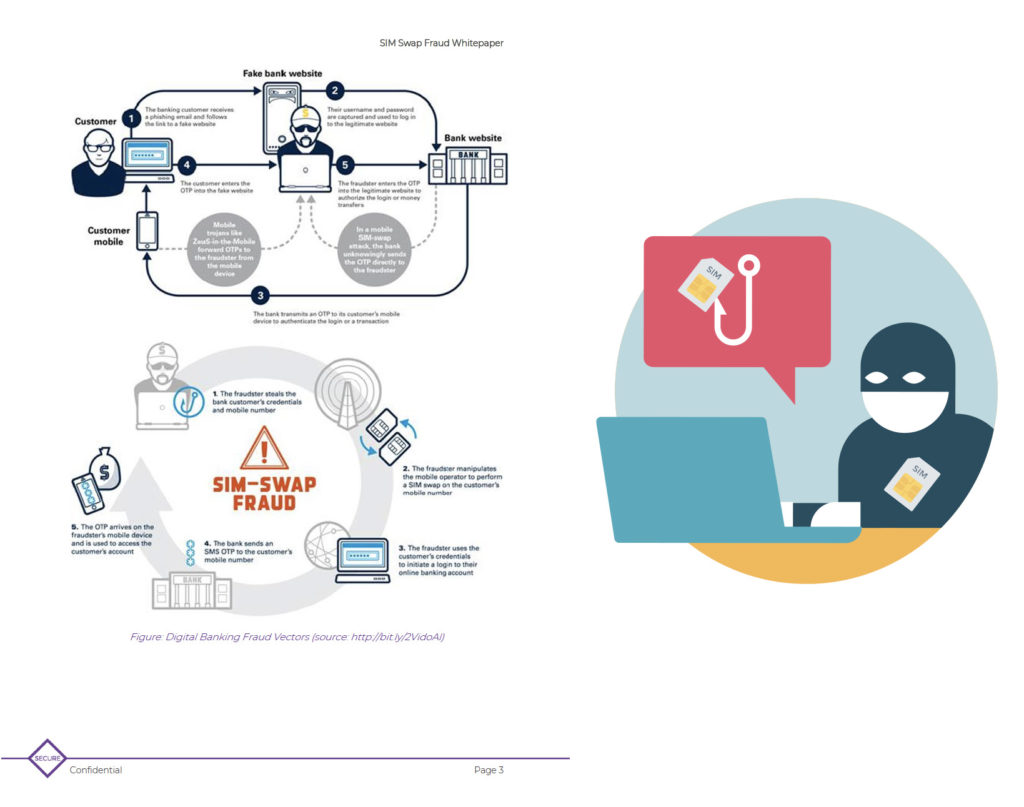
Sim Swap Fraud
What is SIM swap scam SIM swap scam (also known as SIM jacking, SIM splitting, or Port-Out scam) is a type of account takeover fraud that exploits the weakness in conventional methods of two-factor authentication/verification. More often than not, this attack… Read More
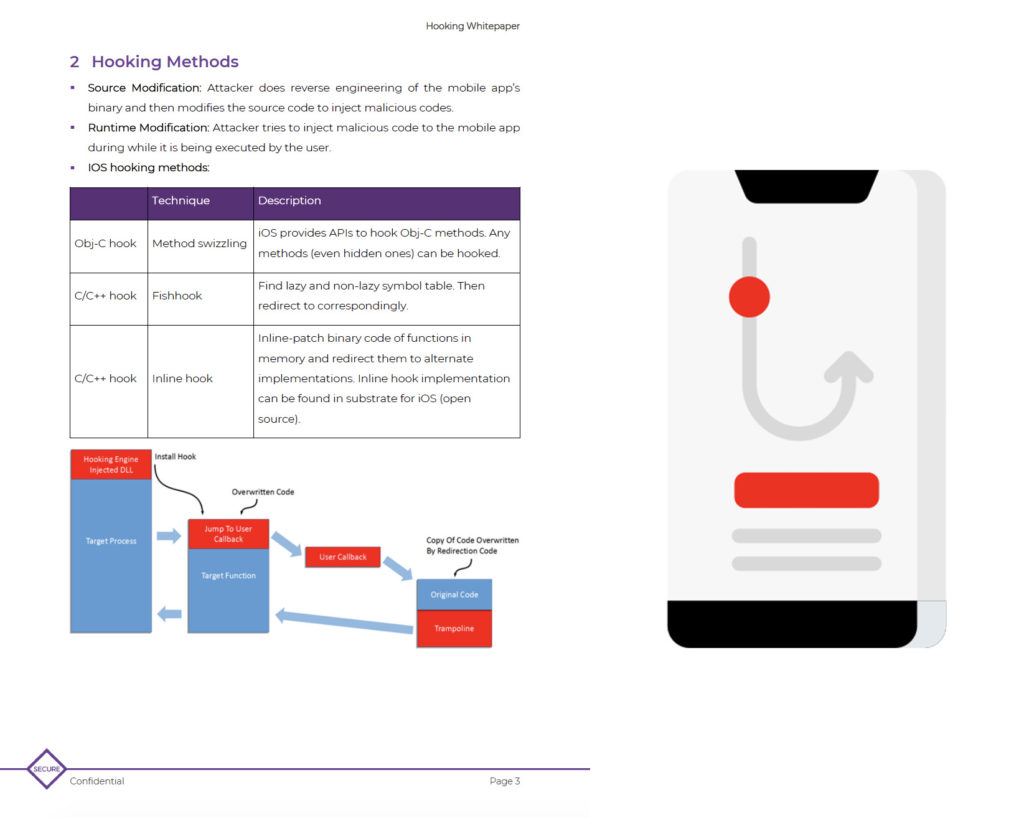
Application Hooking
What is Hooking Hooking is a term for a range of code modification/tampering techniques that are used to change the behaviour of the original code running sequence by inserting instructions into the code segment at runtime. Find out from this whitepaper why… Read More
