An Inside Look at Scams and Countermeasures
September 2023 – Mobile malware attacks are once again on the rise in Singapore, with Android users being the primary targets. These attacks typically begin with enticing advertisements spread across various social media platforms such as Facebook and Instagram. These ads lure victims in with attractive promotions, often related to food delivery and cleaning services. To avail of these offers, victims are directed to click on a link, which connects them to scammers via WhatsApp. The scammers then request the installation of a mobile app and a SGD 5 deposit to confirm the order. Unfortunately, the installation of this app grants the attackers control over the victim’s device, leading to potential bank account breaches.
As a cybersecurity solutions consultant, I decided to delve deeper into the world of scammers by engaging with one myself.
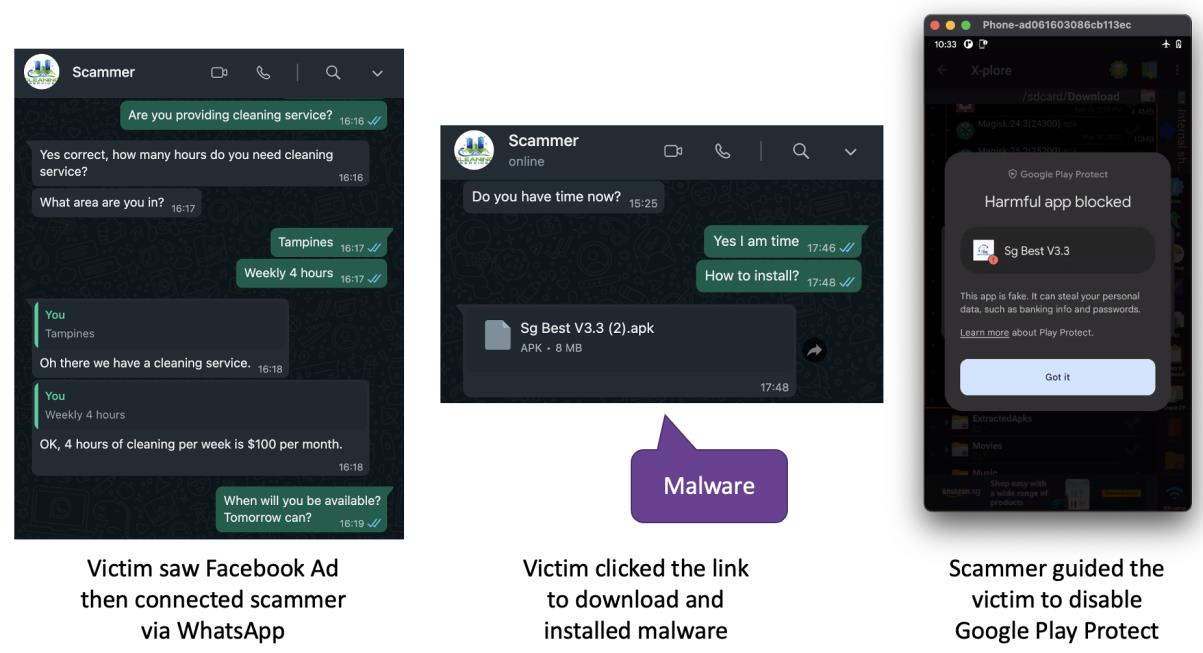
It all started with a Facebook advertisement for a home cleaning service. Clicking on the link led me to the scammer via WhatsApp. Assuming that English would suffice for communication, I initiated a conversation about the service, scheduling, and pricing. However, after providing an incomplete residential address, the scammer generated an invoice without realising the address didn’t make sense. He then insisted on the installation of a mobile app by sharing an APK file via WhatsApp.
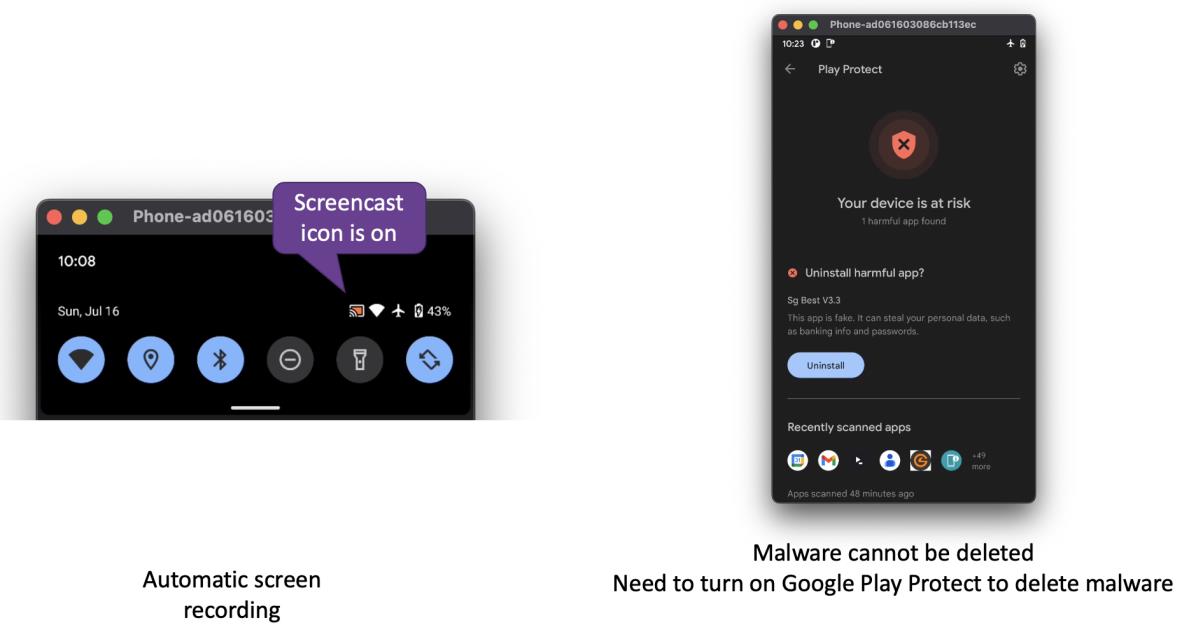
During our conversation, the scammer struggled to express himself in English and requested that we switch to Mandarin. The mobile app, named Sg Best V3.3, demanded full control over my phone. I became suspicious when I noticed a little red icon indicating that screencasting was in progress, allowing the attacker to view everything on my device. Upon launching the app, it displayed a cleaner company name different from the one claimed by the scammer. When I attempted to uninstall the app, I encountered difficulties due to administrator privileges. Eventually, I resorted to turning on Google Play Protect to detect and remove the malware.
With the APK file in my possession, I conducted a static analysis, which revealed that the app could not run in an emulator, requiring a physical phone. If the phone were rooted, installation would be even easier. Surprisingly, there were no warnings from Google Play Protect. Using a simple tool, I discovered that the app had access to 15 dangerous permissions, including reading SMS, accessing location data, and recording audio.
- Send SMS
- Read SMS
- Read Call Log
- Read Contacts
- Get Accounts
- Camera
- Record Audio
- Access Coarse Location
- Access Fine Location
- Call Phone
- Read External Storage
- Write External Storage
- Read Phone State
- Read Calendar
- 1Write Calendar
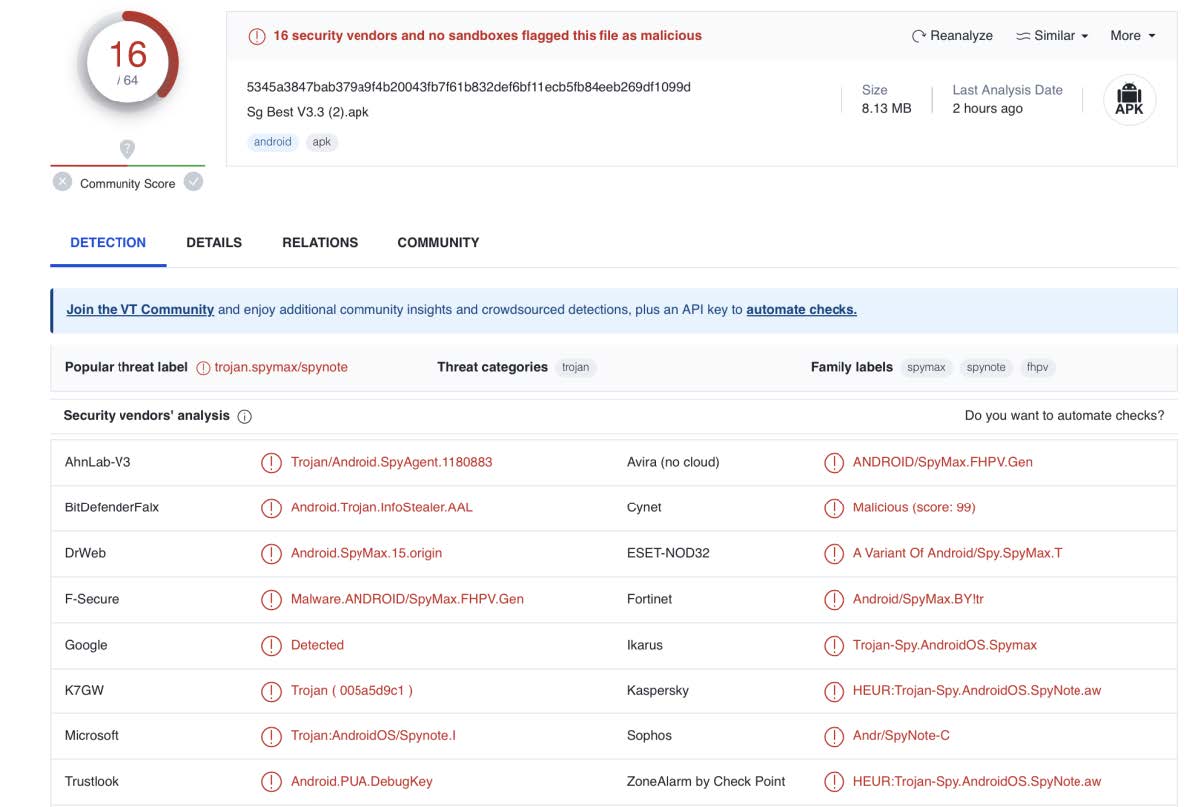
Uploading the APK file to VirusTotal confirmed that it was a trojan horse designed to extract sensitive information from compromised devices.
Note that the mobile app users are not the only ones affected by this scam. Legitimate cleaning service providers have also received numerous complaints about scams, resulting in many customers switching to other service providers.

After investigating several fake advertisements, I noticed that some of them connected to the same WhatsApp account. Furthermore, the scammers recognised when the same person contacted them multiple times, even leaving scolding voice messages. It appears that these scammers are part of the same group, constantly evolving their tactics.
Despite multiple reports of these attacks over the years, people continue to fall victim to scams. While educating the public about the dangers of scammers is essential, hardening mobile banking apps against attacks remains the most effective strategy. Enabling Multi-Factor Authentication (MFA) is a proven method to protect against account takeover. However, not all MFAs are equal. Authentication relies on three factors: what you know, what you have, and who you are. When attackers phish for information, they gain knowledge about what you know. Monitoring your device for one-time passwords (OTPs) gives them access to what you have. Among these factors, biometrics requires the most technical skills to compromise.
Ultimately, achieving absolute resistance to cyberattacks remains a complex challenge. However, it’s important to note that mobile technologies capable of providing ultra-high-security solutions do exist. In addition to MFA, hardening banking apps to detect unauthorised access and respond to malware attacks effectively safeguards end users from financial loss. When combined with a comprehensive set of physical, technical, and administrative controls, they create a formidable defense against attackers seeking to compromise the system while enhancing the bank’s reputation for customer-first security.
Chi Wai Hui is a seasoned Mobile App Security Expert with extensive experience in the cybersecurity field. As a CISSP and ACLP Certified Trainer, he has over a decade of expertise in providing cutting-edge security solutions, conducting training and workshops, and advocating for the importance of App Identity, Device Identity, and User Identity. His impressive career includes roles at renowned organizations such as V-Key, IDEMIA, and Gemalto, where he has consistently demonstrated his commitment to mobile app security and authentication, making him a valuable asset in the industry.
ABOUT V-KEY
V-Key’s pioneering mobile technology powers ultra-high-security solutions for mobile identity, authentication, authorization, and payments for major banks, payment gateways, and government agencies. The V-OS Smart Token family is a versatile, highly secure second-factor authentication and authorization solution for mobile devices. They are a flexible and cost-effective alternative to traditional hardware Time Password (OTP) tokens and OTP-delivered SMS. Moreover, the V-OS Smart Token family offers a much more efficient authentication process than traditional methods, allowing for quick and secure authentication of customers. It is becoming increasingly important for banks as digital transactions grow. Additionally, V-OS Smart Token can be used to quickly confirm transactions, helping to reduce the risk of fraud and data theft.